At Microsoft Ignite 2019, we announced the preview of more than 15 new features. This blog provides an update for the features that are now generally available to our customers.
As the world comes together to combat COVID-19, and remote work becomes a critical capability for many companies, it’s extremely important to maintain the security posture of your cloud assets while enabling more remote workers to access them.
Azure Security Center can help prioritize the actions you need to take to protect your security posture and provide threat protection for all your cloud resources.
Enhanced threat protection for your cloud resources with Azure Security Center
Azure Security Center continues to extend its threat protection capabilities to counter sophisticated threats on cloud platforms:
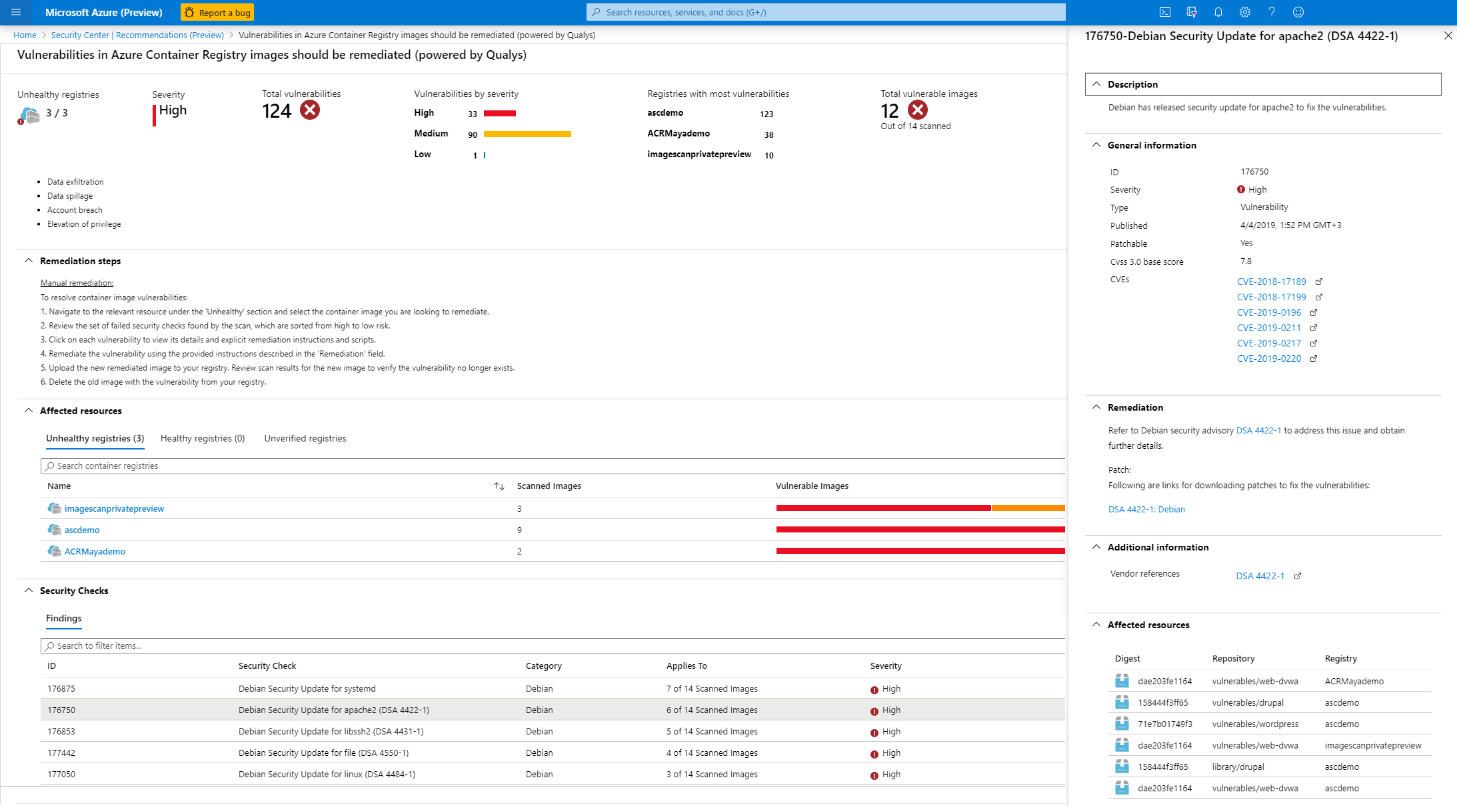
Scan container images in Azure Container Registry for vulnerabilities generally available
Azure Security Center can scan container images in Azure Container Registry (ACR) for vulnerabilities.
The image scanning works by parsing through the packages or other dependencies defined in the container image file, then checking to see whether there are any known vulnerabilities in those packages or dependencies (powered by a Qualys vulnerability assessment database).
The scan is automatically triggered when pushing new container images to Azure Container Registry. Found vulnerabilities will surface as Security Center recommendations and be included in the Secure Score together with information on how to patch them to reduce the attack surface they allowed.
Since we launched the preview at Ignite 2019, registered subscriptions initiated over 1.5 million container image scans. We have carefully analyzed the feedback we received and incorporated it into this generally available version. We have added scanning status to reflect the progress of the scan (Unscanned, Scan in progress, Scan error, and Completed) and improved the user experience based on the feedback we've received from you.
Threat protection for Azure Kubernetes Service Support in Security Center generally available
The popular, open source, platform Kubernetes has been adopted so widely that it is now an industry standard for container orchestration. Despite this widespread implementation, there’s still a lack of understanding regarding how to secure a Kubernetes environment. Defending the attack surfaces of a containerized application requires expertise. You need to ensure the infrastructure is configured securely, and constantly monitor for potential threats. Support for Security Center Azure Kubernetes Service (AKS) is now generally available.
The capabilities include:
- Discovery and Visibility: Continuous discovery of managed AKS instances within Security Center’s registered subscriptions.
- Secure Score recommendations: Actionable items to help customers comply with security best practices in AKS as part of the customer’s Secure Score, such as "Role-Based Access Control should be used to restrict access to a Kubernetes Service Cluster."
- Threat Protection: Host and cluster-based analytics, such as “A privileged container detected.”
For the generally available release, we've added new alerts (for the full list please visit Alerts for Azure Kubernetes Service clusters and Alerts for containers – host level sections of the alerts reference table), and alert details were fine tuned to reduce false positives.
Cloud security posture management enhancements
Misconfiguration is the most common cause of security breaches for cloud workloads. Azure Security Center provides you with a bird’s eye security posture view across your Azure environment, enabling you to continuously monitor and improve your security posture using the Azure Secure Score. Security Center helps manage and enforce your security policies to identify and fix such misconfigurations across your different resources and maintain compliance. We continue to expand our resource coverage and the depth insights that are available in security posture management.
Support for custom policies generally available
Our customers have been wanting to extend their current security assessments coverage in Security Center with their own security assessments based on policies that they create in Azure Policy. With support for custom policies, this is now possible.
We're also announcing that Azure Security Center’s support for custom policies is generally available. These new policies will be part of the Azure Security Center recommendations experience, Secure Score, and the regulatory compliance standards dashboard. With the support for custom policies, you are now able to create a custom initiative in Azure policy and add it as a policy in Azure Security Center through a simple click-through onboarding experience and visualize them as recommendations.
For this release, we've added the ability to edit the custom recommendation metadata to include severity, remediation steps, threat information, and more.
Assessment API generally available
We are introducing a new API to get Azure Security Center recommendations with information and provide you the reason why assessments failed. The new API includes two APIS:
- Assessments metadata API: Gets recommendation metadata.
- Assessments API: Provides the assessment results of each recommendation on a resource.
We advise that our customers using the existing Tasks API should use the new Assessments API for their reporting.
Regulatory compliance dynamic compliance packages generally available
You can now add ‘dynamic compliance packages,’ or additional standards beyond the ‘built-in’ compliance packages in regulatory compliance.
The regulatory compliance dashboard in Azure Security Center provides insights into your compliance posture relative to a set of industry standards, regulations, and benchmarks. Assessments continually monitor the security state of your resources and are used to analyze how well your environment is meeting the requirements for specific compliance controls. Those assessments also include actionable recommendations for how to remediate the state of your resources and thus improve your compliance status.
Initially, the compliance dashboard included a very limited set of standards that were ‘built-in’ to the dashboard and relied on a static set of rules included with Security Center. With the dynamic compliance packages feature, you can add new standards and benchmarks that are important to you to your dashboard. Compliance packages are essentially initiatives defined in Azure Policy. When you add a compliance package to your subscription or management group from the ASC Security Policy, that essentially assigns the regulatory initiative to your selected scope (subscription or management group). You can see that standard or benchmark appear in your compliance dashboard with all associated compliance data mapped as assessments.
In this way, you can track newly published regulatory initiatives as compliance standards in your Security Center regulatory compliance dashboard, Additionally, when Microsoft releases new content for the initiative (new policies that map to more controls in the standard), the additional content appears automatically in your dashboard. You are also able to download a summary report for any of the standards that have been onboarded to your dashboard.
There are several supported regulatory standards and benchmarks that can be onboarded to your dashboard. The newest one is the Azure Security Benchmark, which is the Microsoft-authored Azure-specific guidelines for security and compliance best practices based on common compliance frameworks. Additional standards will be supported by the dashboard as they become available.
For more information about dynamic compliance packages, see the documentation here.
Workflow automation with Azure Logic Apps generally available
Organizations with centrally managed security and IT operations implement internal workflow processes to drive required action within the organization when discrepancies are discovered in their environments. In many cases, these workflows are repeatable processes and automation can greatly reduce overhead streamline processes within the organization.
Workflow automation in Azure Security Center, now generally available, allows customers to create automation configurations leveraging Azure Logic Apps and to create policies that will automatically trigger them based on specific Security Center findings such as Recommendations or Alerts. Azure Logic App can be configured to do any custom action supported by the vast community of Logic App connectors or use one of the templates provided by Security Center such as sending an email. In addition, users are now able to manually trigger a Logic App on an individual alert or recommendation directly from the recommendation (with a ‘quick fix’ option) or alert page in Azure Security Center.
Advanced integrations with export of Security Center recommendations and alerts generally available
The continuous export feature of Azure Security Center, which supports the export of your security alerts and recommendations, is now generally available, also via policies. Use it to easily connect the security data from your Security Center environment to the monitoring tools used by your organization, by exporting to Azure Event Hubs or Azure Log Analytics workspaces.
This capability supports enterprise-scale scenarios, among others, via the following integrations:
- Export to Azure Event Hubs enables integration with Azure Sentinel, third party SIEMs, Azure Data Explorer, and Azure Functions.
- Export to Azure Log Analytics workspaces enables integration with Microsoft Power BI, custom dashboards, and Azure Monitor.
For more information, read about continuous export.
Building a secure foundation
With these additions, Azure continues to provide a secure foundation and gives you built-in native security tools and intelligent insights to help you rapidly improve your security posture in the cloud. Azure Security Center strengthens its role as the unified security management and advanced threat protection solution for your hybrid cloud.
Security can’t wait. Get started with Azure Security Center today and visit Azure Security Center Tech Community, where you can engage with other security-minded users like yourselves.